
Fluxless TCB vs TCB
As interconnection pitches shrink below 10µm for advanced logic and memory applications, fluxless TCB solves the issues that standard TCB encounters with the flux.
A digital certificate is an electronic ID card that proves the authenticity of websites and online services. Just like you have a physical ID card to prove your identity, websites and online services use digital certificates to prove their identity on the internet.
Here’s how it works in a simple way:
SolarWinds is a software company that provides network management and monitoring tools to thousands of organizations worldwide, including government agencies and major corporations. The attackers targeted SolarWinds’ Orion platform, a widely used network management tool.
The Role of Digital Certificates: The attackers, believed to be a Russian state-sponsored hacking group known as APT29 or Cozy Bear, managed to compromise SolarWinds’ software build system. They injected a malicious code (malware) into a legitimate software update for the Orion platform. This malicious update was then signed with a legitimate SolarWinds digital certificate, making it appear as a genuine and trusted update.
How It Worked:
Impact: As a result of this attack, numerous government agencies, private companies, and organizations unknowingly installed the compromised software update. The attackers had access to sensitive information and networks for an extended period, compromising national security and sensitive corporate data.
Response and Mitigation: Once the attack was discovered, organizations took immediate action to remove the compromised software and strengthen their cybersecurity measures. SolarWinds revoked the compromised digital certificate and worked to enhance the security of its software development process.
This case illustrates the critical role that digital certificates play in cybersecurity. Attackers can exploit trust in digital certificates to infiltrate systems, making it essential for organizations to continually monitor and secure their digital certificate infrastructure to prevent such incidents.
Key industries that leverage digital certificates are:
1. E-commerce: In the fast-paced world of e-commerce, digital certificates are instrumental in securing online transactions and safeguarding sensitive customer data, including credit card information. Customers rely on digital certificates to assure them that their online purchases occur on authentic and secure platforms. E-commerce involves the exchange of financial information, such as credit card numbers and banking details, between customers and online retailers. Ensuring the security of these transactions is essential to prevent fraudulent activities, unauthorized charges, and financial losses for both customers and businesses.
2. Online Banking: Digital certificates are indispensable for the financial sector. They guarantee the authenticity and online security of a bank’s website, providing customers with the confidence that their financial transactions and personal information are well-protected. A bank account typically holds an individual’s or business’s financial assets, including savings, investments, and funds for everyday expenses. Ensuring the security of these assets is fundamental to safeguarding one’s financial well-being.
3. Healthcare: Within the healthcare industry, where patient confidentiality is paramount, digital certificates play a pivotal role. They secure patient information, ensuring that only authorized individuals have access to sensitive data. This is crucial for maintaining patient privacy and adhering to stringent regulatory standards.
4. Government Agencies: Government websites are often accessed for critical services and information. Digital certificates are a cornerstone in verifying the identity of users and securing the data exchanged on government portals, contributing to enhanced cybersecurity and trustworthiness.
1980s: The Birth of Public Key Cryptography In the 1980s, a groundbreaking development in the field of cybersecurity emerged with the invention of public key cryptography. This innovative cryptographic system introduced the concept of using pairs of keys: a public key for encryption and a private key for decryption. Among the pioneering cryptosystems of this era, the RSA algorithm, conceived by Ron Rivest, Adi Shamir, and Leonard Adleman, stood out as one of the earliest and most influential. This breakthrough laid the foundation for the future of digital certificates.
1990s: The Rise of SSL and Digital Certificates As the internet started to gain momentum in the early 1990s, Netscape Communications introduced the Secure Sockets Layer (SSL) protocol, a pivotal moment that paved the way for secure online communication. SSL leveraged digital certificates to authenticate and encrypt data exchanged between web servers and clients. This development led to the birth of the now-ubiquitous HTTPS protocol. SSL’s reliance on digital certificates marked a significant milestone in ensuring the security of online transactions and establishing trust on the internet.
2000s: Certification Authorities and X.509 Standardization The 2000s witnessed a surge in the adoption of digital certificates, driven by the booming e-commerce industry and the increasing prevalence of online services. Certification authorities (CAs) emerged as trusted entities responsible for issuing and managing digital certificates. The industry embraced the X.509 certificate format as a standardized framework, ensuring interoperability among different certificate authorities and applications. This standardization bolstered the credibility and consistency of digital certificates across the digital landscape.
2010s: Expanding Horizons for Digital Certificates In the 2010s, digital certificates continued to evolve in response to the ever-changing internet landscape. Beyond securing websites, digital certificates became crucial for safeguarding other critical infrastructure, including cloud services, mobile applications, and the burgeoning Internet of Things (IoT) ecosystem. These certificates played a pivotal role in ensuring secure communication channels and verifying the identities of all participating entities.
The decade also witnessed the transition from SSL to the more robust Transport Layer Security (TLS) protocol. TLS, succeeding SSL, significantly enhanced the security of digital certificates, providing better protection against cyber threats.
Today: Digital Certificates as Cornerstones of Internet Security Digital certificates have become indispensable components of internet security. Their extensive use includes establishing secure connections, verifying the authenticity of websites, encrypting sensitive data transmission, and authenticating users. With the adoption of the TLS protocol, the security of digital certificates has reached new heights.

As interconnection pitches shrink below 10µm for advanced logic and memory applications, fluxless TCB solves the issues that standard TCB encounters with the flux.
The metal pitch refers to the distance between the centers of two adjacent metal interconnect lines on an integrated circuit (IC). Since transistors evolved into 3D strucrures, this measurement has lost significance.
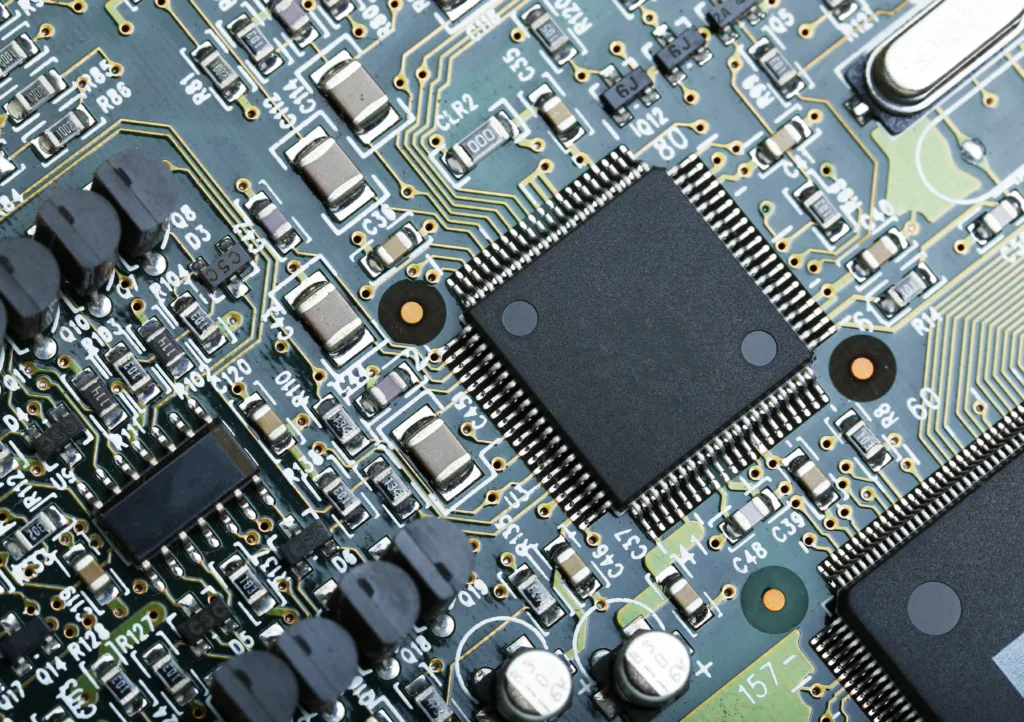
The front-end and back-end are highly interdependent. A constant feedback loop between front and back-end engineers is necessary to improve manufacturing yields.
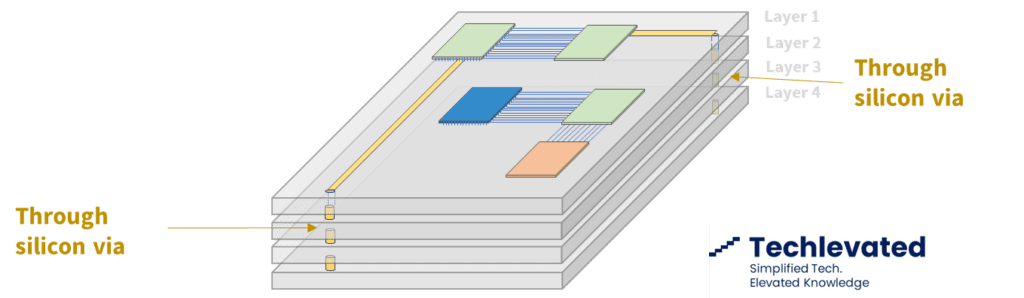
Built directly into the silicon, through silicon vias (TSV) facilitate 3D IC integration and allow for more compact packaging. They have become the default solution to interconnect different chip layers or to stack chips vertically.
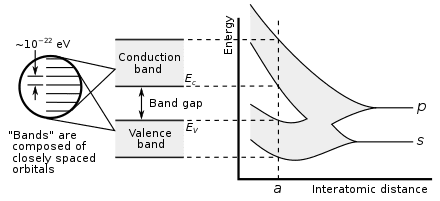
Silicon carbide (SiC) is used in electric vehicles due to its wide bandgap and great thermal conductivity. Gallium nitride (GaN) shares many characteristics with SiC while also minimizing RF noise.
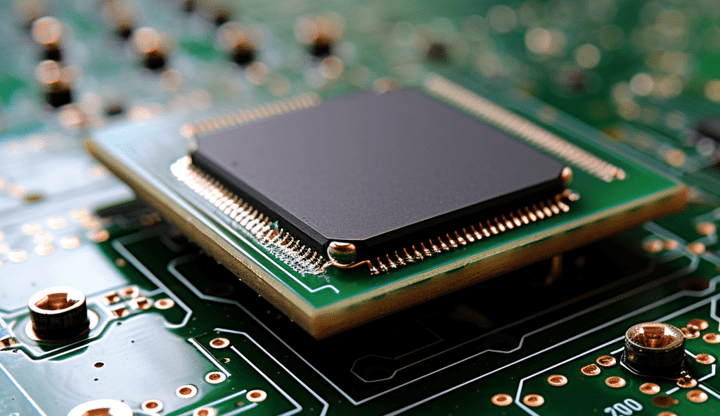
GPU vs CPU is a parallelization vs complexity dilemma. While GPUs can manage very large parallel calculations, they struggle with linear, more heterogeneous tasks, where CPUs excel.